Our Insights
Innovative Ways - Satisfied Clientele
Innovative Ways - Satisfied Clientele

Kapil Panchal - August 18, 2020
If you’re planning on starting your very own eCommerce website, you must think about security. You want your website to grow and flourish. In order to successfully achieve this, you have to be sufficiently protected at all times. Sadly, many new start-ups forget about this highly important aspect. To ensure that you don’t miss out on the best security, we’re going to share with you some great ways that you can start protecting yourself right away. But before we get to the tips, let’s take...

iFour Team - November 07, 2017
Many times it happens that you get a link via mail or social media and when you directly click on that link you are fortunately directed towards some wrong website which is not supposed to be. This is an example of Unvalidated redirects and forwards as per software development companies. Unvalidated redirects and forwards is ranked 10th on the list of OWASP top 10 vulnerabilities 2013. In this vulnerability a web application accepts untrusted source which could cause the web application...
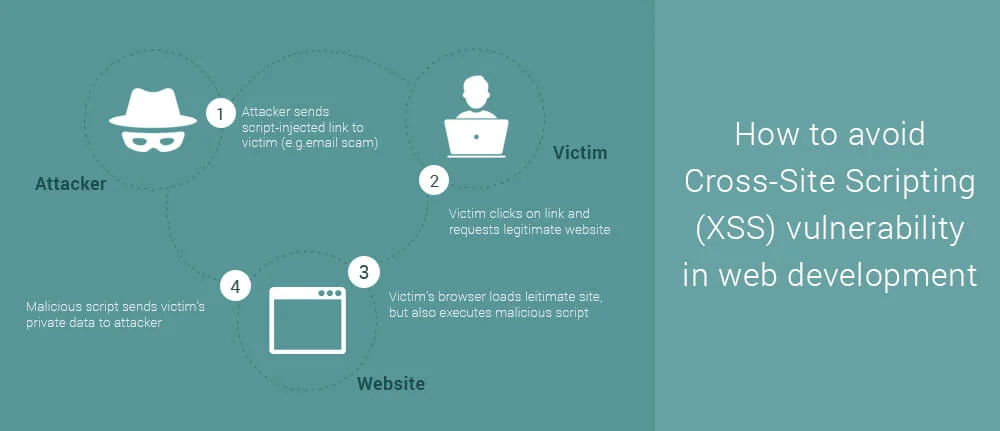
iFour Team - November 07, 2017
Cross-site scripting is ranked 3rd in the list of OWASP top 10 vulnerabilities 2017. Cross-site scripting are one of the most rampant occurring injection attacks faced by various web application across businesses. That’s why to know the causes of XSS, its impact and prevention is must. What is Cross-site Scripting? Cross-site scripting attacks are types of injection, in which malicious scripts are injected into trusted web applications. This attack happens when a hacker uses...

iFour Team - September 05, 2017
It has become necessary to understand the importance of security for any company including software development companies in order to provide robust, safe and secure experience to users. Actually hacking is not that much of dramatic which are shown in movies. It is dangerous enough that every business owners would be wanting to avoid it. In this blog we would try to know what is malware, how it can affect web applications and computer systems and some suggestions to protect your environment...

iFour Team - September 05, 2017
‘Insecure direct object references’ is ranked 4th on the list OWASP top 10 vulnerabilities 2013. Now days, it has become a serious concern for software development companies to maintain the privacy of all the users. This vulnerability breaches the authorization gates and allow an attacker to thieve unauthorized data from web application. Let’s have detailed understanding of this vulnerability . What is insecure direct object references? According to OWASP definition insecure...