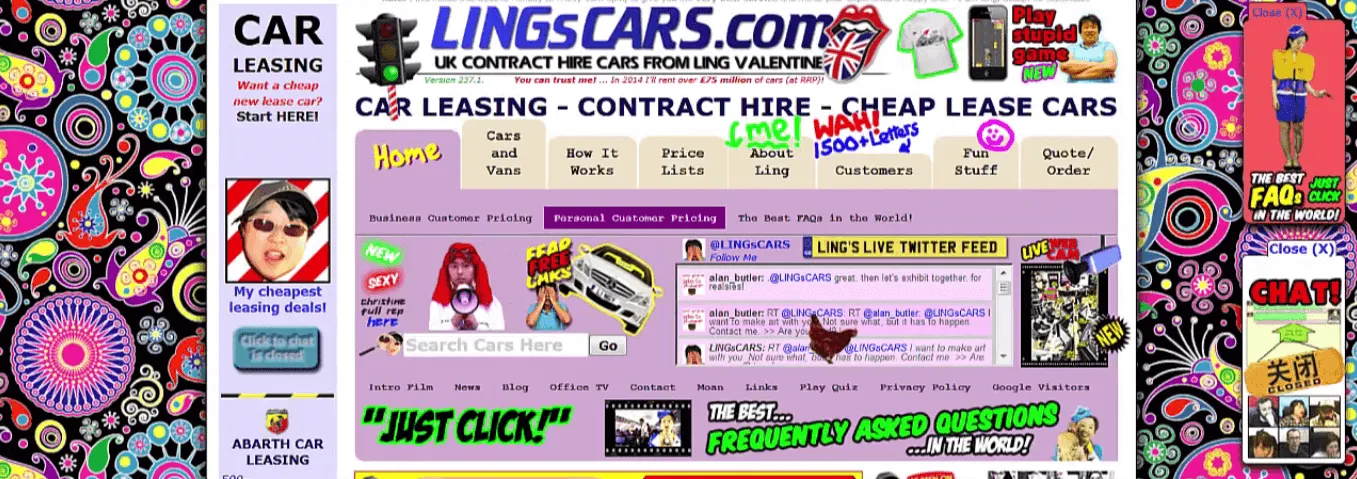
Many times it happens that you get a link via mail or social media and when you directly click on that link you are fortunately directed towards some wrong website which is not supposed to be. This is an example of Unvalidated redirects and forwards as per software development companies.
Unvalidated redirects and forwards is ranked 10th on the list of OWASP top 10 vulnerabilities 2013. In this vulnerability a web application accepts untrusted source which could cause the web application to redirect on any untrusted web application. On modifying that untrusted URL source to a malicious site, the attacker can do any phishing scam and steal any sensitive user data. Here websites many times forward or redirect users to any other web pages and use untrusted data to identify the destination pages. Without any proper validation, attackers redirects victims to malware sites or uses forwards to have the access of unauthorized pages.