Power BI Report Server: Key Features and Elements
Every CTO knows the struggle of managing complex reports. The inefficiency of scattered data, the constant juggling between reporting tools, the challenge of ensuring accurate KPIs...
iFour Team - June 19, 2019
Listening is fun too.
Straighten your back and cherish with coffee - PLAY !
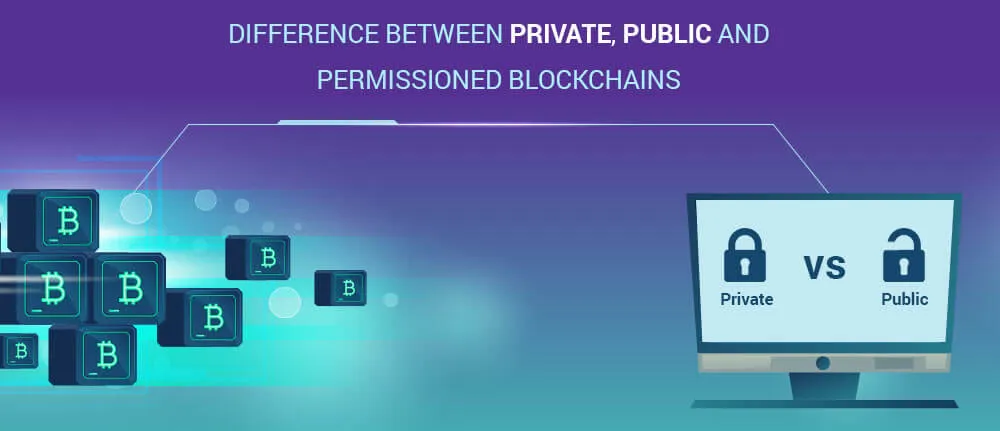
The Blockchain has considerably showcased its extensiveness in laying solutions to the essential market issues like security, transparency, accountability, time consumption, value and more.
Every Custom Blockchain development Company has witnessed the big play of blockchain in improving the efficiency and effectiveness of the industry function.
A Blockchain is maintained on a decentralized and distributed network of computers. There are few flavors of blockchain that have emerged in recent years.
Blockchain has three types of network:
All having their own advantages, depending upon the situation Blockchain platform is required for use. To utilize the best suited one, understanding each one of them is important.
As the name suggests, public network is open to all. It can be joined by anyone with all the access rights to read, write and validate the blocks. Each entity participating in the network is known as a node.
In public network, identity of nodes is not known and there can be several advantages of it.
Examples: Bitcoin is the best known example of public network. Other cryptocurrencies following public network are Ethereum, Litecoin, etc.
This kind of architecture is not good for enterprises as they want only limited people present in their organization to access the data they share and that too by their roles. Private network can be followed to achieve this aspect.
A central authority decides who can read/write/verify transactions. This kind of architecture is followed by an organization to keep data limited to the authority. Public read access may be allowed.
Examples: Hyperledger, Hashgraph, R3 Corda, etc.
Real-life example:
A person dealing with various suppliers must want to hide the contracts signed with another supplier. The financial details from the customers must also be kept hidden thus different rights to different users can be provided in private network.
There is a thin line gap in private and permissioned network. Private network has a single organization as a central authority while permissioned network has multiple organizations as a central authority.
Multiple organizations involving in this process must have trust on each other to read/write and validate transactions.
Every CTO knows the struggle of managing complex reports. The inefficiency of scattered data, the constant juggling between reporting tools, the challenge of ensuring accurate KPIs...
The very first reason why you should implement Row Level Security is to foster trust, a crucial element for any business's success. Next, it reduces data clutter and helps you load...
The performance of Power BI is significantly influenced by two essential factors: design consistency and the rapid loading of BI elements. This holds true whether you choose Tableau...