Our Insights
Innovative Ways - Satisfied Clientele

We use cookies to improve your experience on our site. Please accept cookies for optimal performance.

601 & 612, The Times square Arcade, Near Baghban party plot, Thaltej - Shilaj Road, Thaltej, Ahmedabad, Gujarat - 380059
Request For a Free Consultation
Innovative Ways - Satisfied Clientele
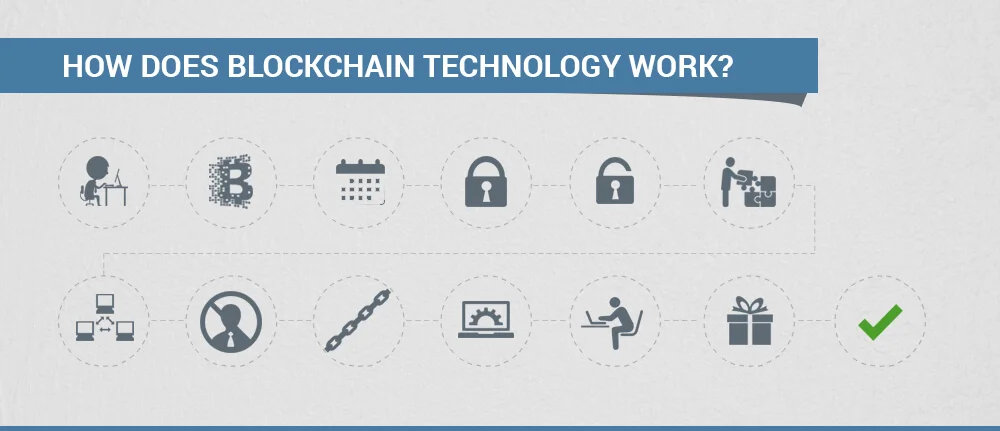
iFour Team - April 23, 2018
The Blockchain is one of the new edge-cutting innovations by Blockchain development company which brought uniqueness crosswise over businesses. This innovation enables distributed exchanges where at least two individuals need to have a common record. It records secure online exchanges through a mutual and ceaselessly accommodated database. What makes blockchains exceptional is that as opposed to being controlled by a solitary association (like Google or Amazon) they are managed by a distributed...

iFour Team - April 02, 2018
Introduction Siri is an Intelligent personal assistant which is own by Apple. It is launched in October, 2011. Siri supports all Apple OS like iOS, watchOS, tvOS and macOS. It is an intelligent part of Apple products. Google Assistant is a Virtual personal assistant which is own by Google. It is launched in May, 2016. It is supports to android OS with smart phone and smart home devices. Currently, most reputed software company in USA is making applications based on Siri and Google...

iFour Team - March 16, 2018
JavaScript Frameworks have transformed the way client-side scripting applications are developed. Several frameworks have evolved with improved features and structures catching the interest of many desktop application development companies. One such framework is React.js, a new version of JavaScript. By adopting a Model-View-Controller (MVC) pattern, these frameworks provide a clear separation of concerns, making code maintenance and scalability easier. The introduction of JavaScript Frameworks...
Recent Posts
Pulumi vs Terraform Explained | IaC Guide for CTOs
September 04, 2025

10 Business Problems You Can Solve Using Dynamics 365 AI
August 27, 2025

Healthcare AI Models In Azure AI: Application & Use cases
August 26, 2025

How to win more deals with AI-Powered Dynamics 365 sales
July 16, 2025

Categories

