Best ways to secure email communication.
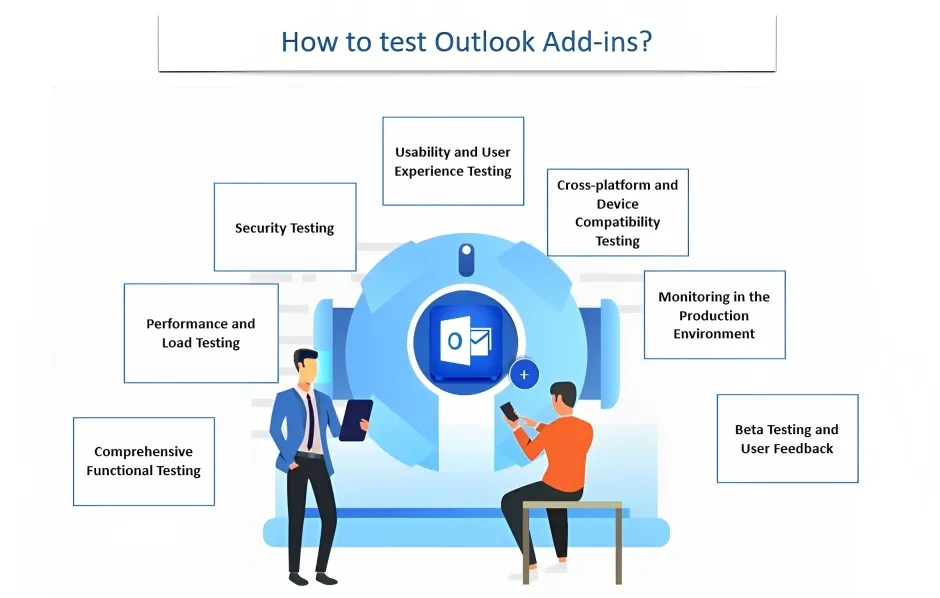
Securing the communication between an Outlook Add-In and a backend server is crucial for maintaining the overall security of the application. Here are some best practices to consider for securing this communication:
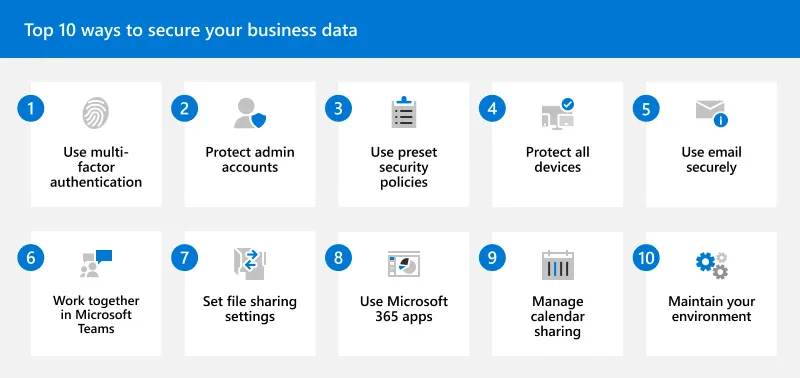
#1 Transport Layer Security (TLS): Use TLS protocols (such as HTTPS) to encrypt the communication between the add-in and the backend server, ensuring confidentiality and integrity of data in transit.
#2 Server certificate validation: Verify the authenticity of the server's SSL/TLS certificate to prevent man-in-the-middle attacks.
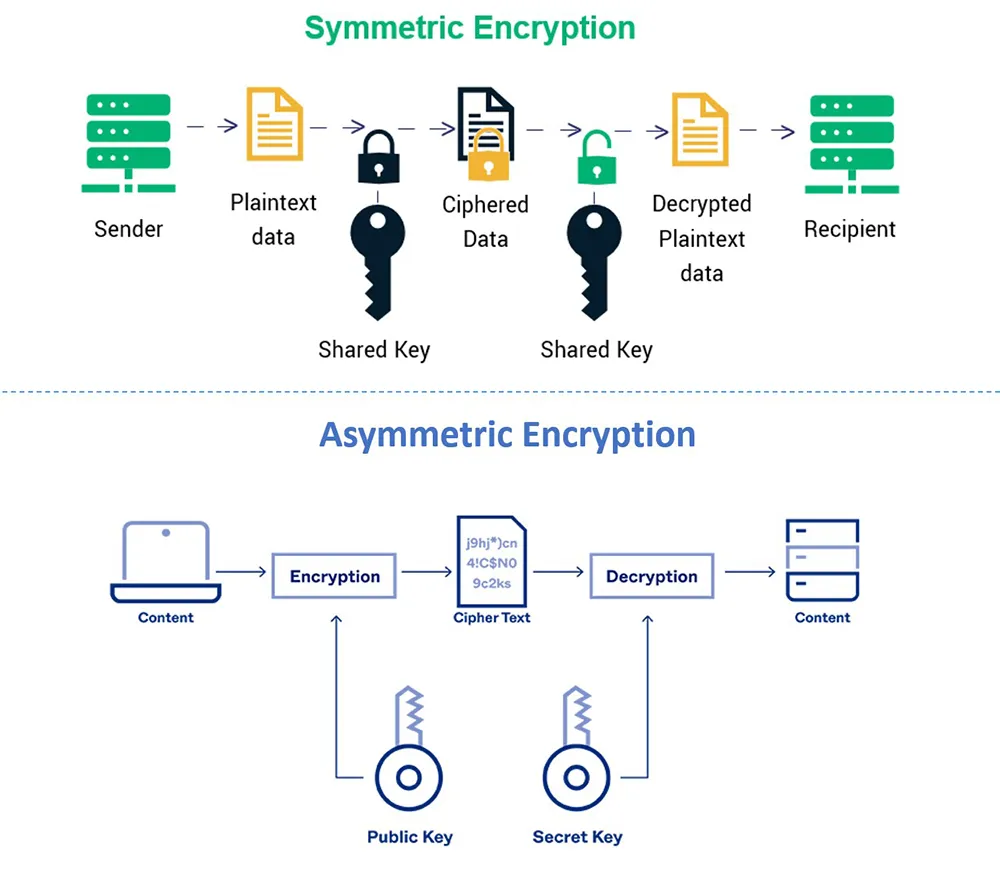
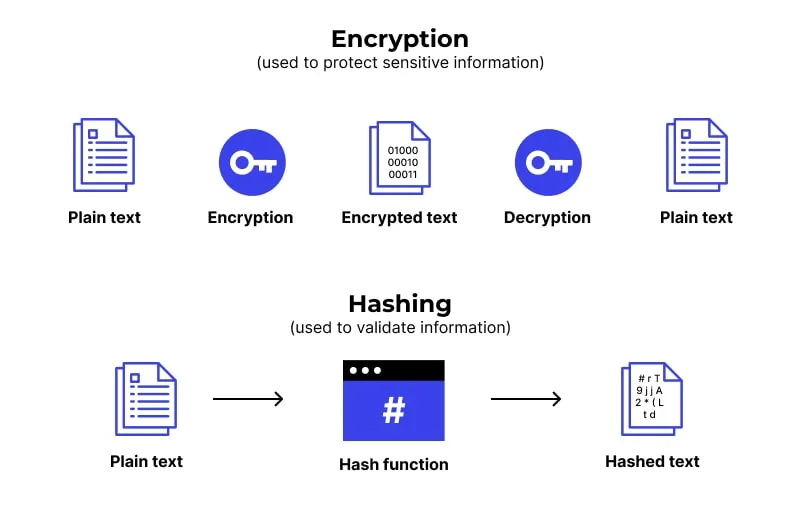
#3 Strong encryption algorithms: Implement strong encryption algorithms (such as AES) to encrypt sensitive data before transmitting it over the network.
#4 Two-way authentication: Implement mutual authentication between the add-in and the backend server using certificates or other secure authentication mechanisms to ensure both parties' identities.
#5 Secure authentication protocols: Use secure authentication protocols (such as OAuth 2.0) to authenticate the add-in with the backend server, preventing unauthorized access.
#6 Input validation and sanitization: Validate and sanitize all input received from the add-in to prevent injection attacks, such as SQL injection or cross-site scripting (XSS).
#7 Access control: Implement proper access controls on the backend server to restrict access to authorized users and prevent unauthorized access to sensitive data.
#8 Secure storage of credentials: Safely store any credentials or tokens required for communication with the backend server, using secure storage mechanisms such as encrypted key stores or secure vaults.
#9 Regular security updates: Keep both the add-in and the backend server up to date with the latest security patches and updates to address any known vulnerabilities.
#10 Security monitoring and logging: To detect and monitor any suspicious actions and potential security breaches, implement effective logging systems. Review and examine the logs often to spot and address security events.
By following these best practices, you can establish a secure and trustworthy communication channel between your Outlook Add-in and the backend server.
It is also worth focusing on secure error handling and logging techniques while Outlook Add-Ins development. Make sure you use robust exception-handling methodologies, error message sanitization to avoid disclosing sensitive information, and logging best practices for non-sensitive information. These measures add a new layer of security to your bespoke Outlook Add-Ins.