1. Introduction
Using Azure Active Directory (Azure AD) B2C, powerful self-service identity management features can be added to desktop app in a few short steps by asp.net software companies USA.
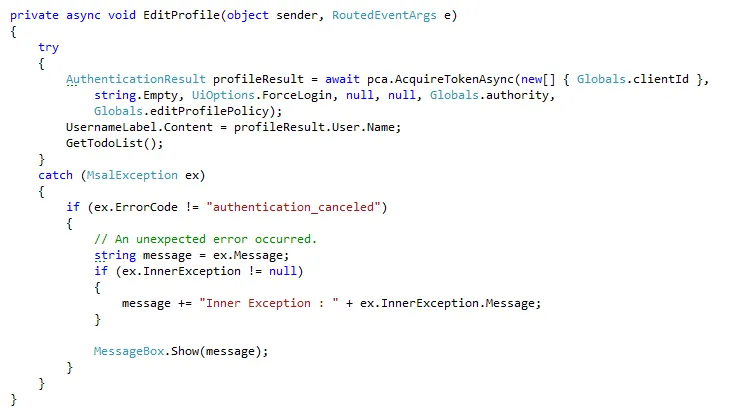
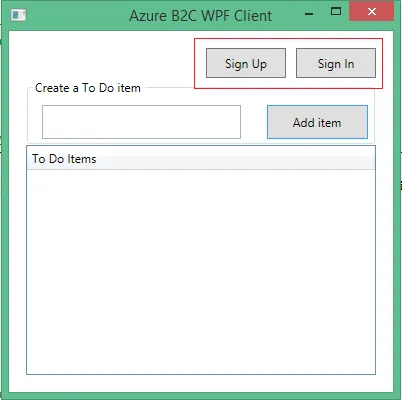
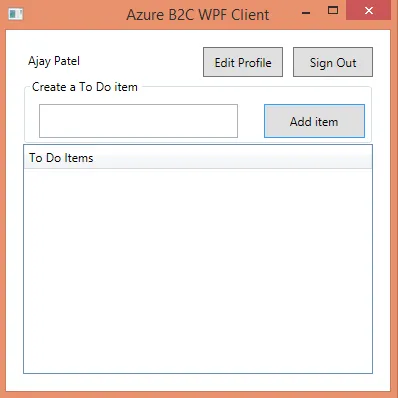
This article shows how to create a .NET Windows Presentation Foundation (WPF) app that includes user sign-up,
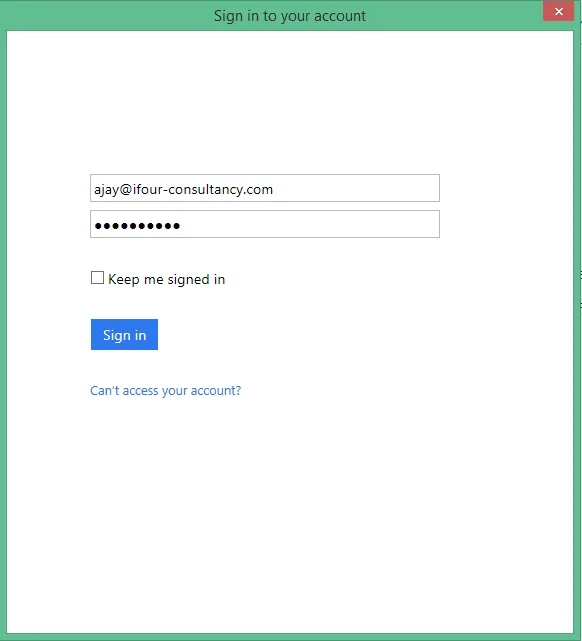
sign-in, and profile management. This app includes support for sign-up and sign-in by using a user name or email. It supports sign-up and sign-in by social accounts such as Facebook and Google.
2. Get an Azure AD B2C Directory
Before using Azure AD B2C, we must create a directory, or tenant. A directory is a container for all of your users, applications, groups, and more. If you don't have directory already then create a B2C directory.
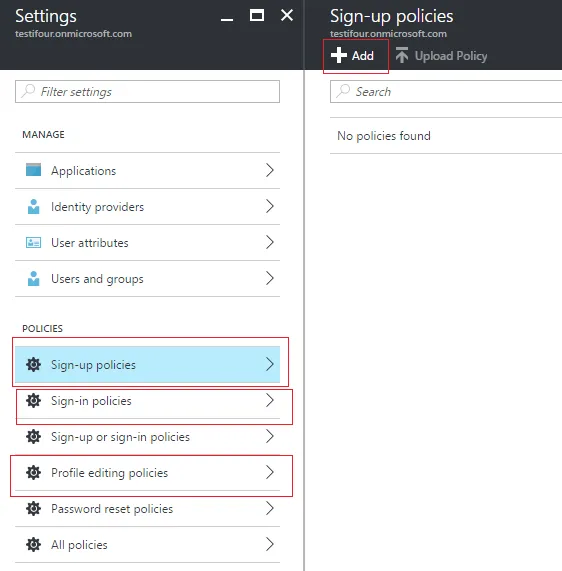
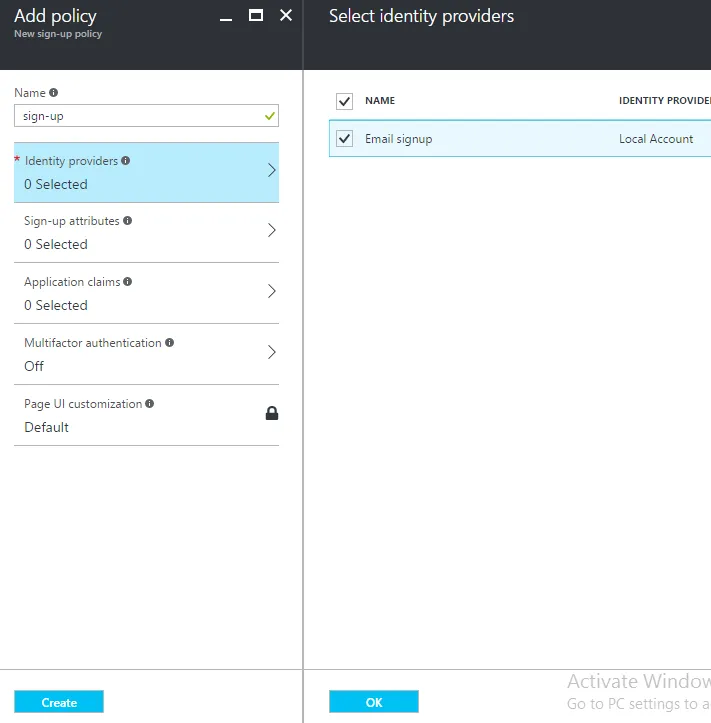
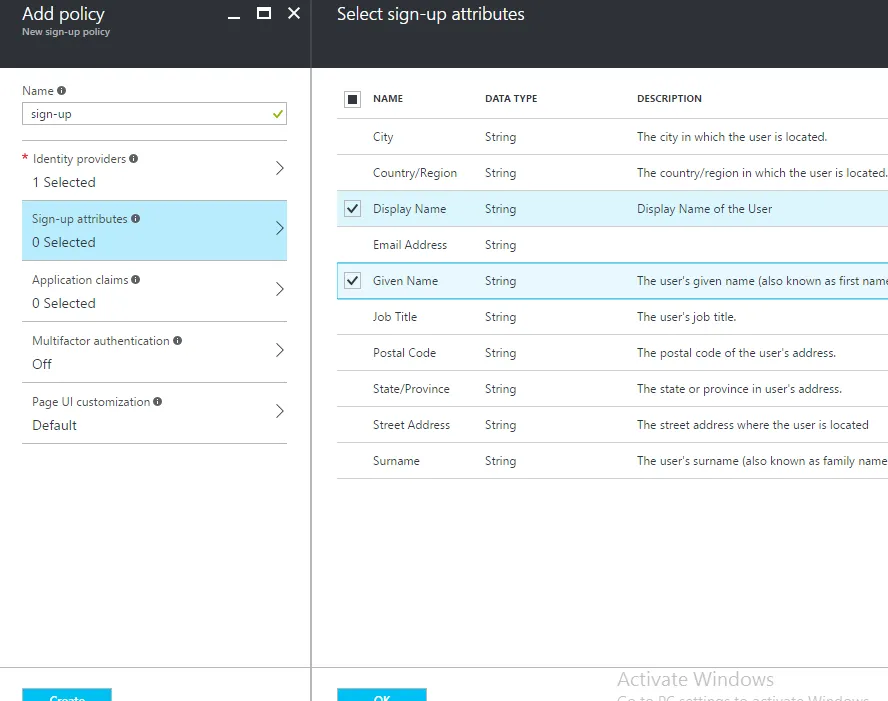
3. Create an Application
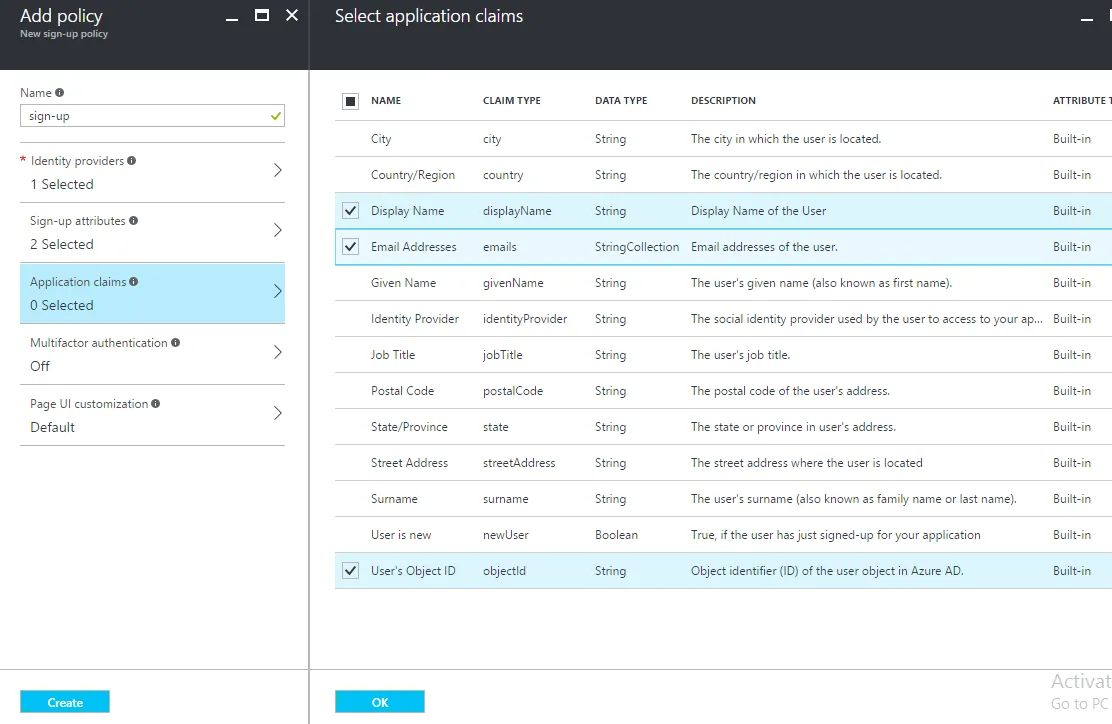
- Next we need to create application in B2C Directory. It gives Azure AD information that need to securely communicate with application. For creating an application in B2C directory follow these steps.
- Make sure to:
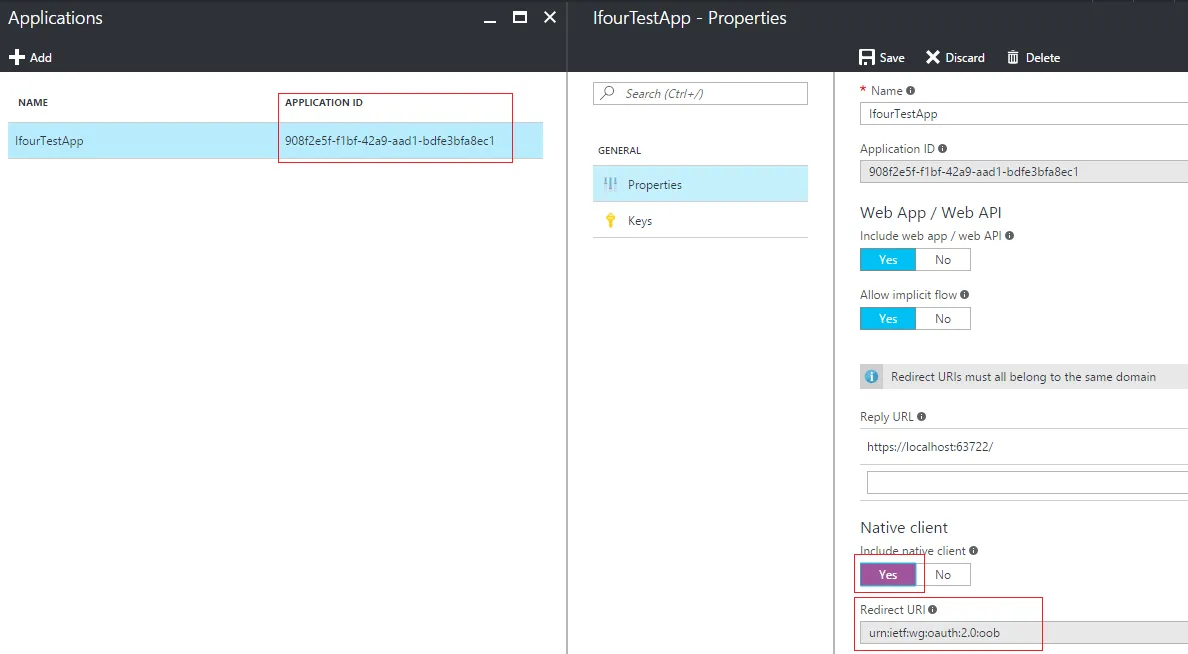
- Include a native client in the application.
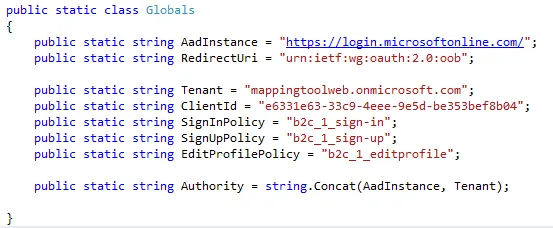
- Copy the Redirect URI urn:ietf:wg:oauth:2.0:oob. It's the default URL for application.
- Copy the Application ID that is assigned to your app. we will need it later.